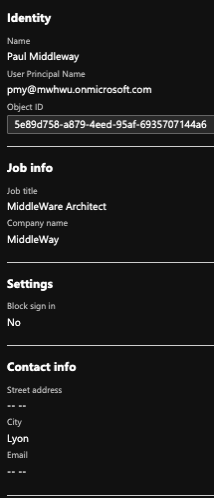
In this blog article, we will show you how to create and update AD users in Azure.
Azure provides us with Identity and Access Management (IAM) services. We can use either Azure AD or Azure AD B2C. Both services are based on the same technologies and are used to log in and access the resources. Azure AD B2C also lets users sign in with their social media accounts (Google, Facebook, etc.). The main difference is that AAD targets internal organizations, while AAD B2C targets customers and consumers.
The following accounts are available:
We can use the AAD Connector to create a user in AAD. This connector is used to connect Logic App to SaaS services:

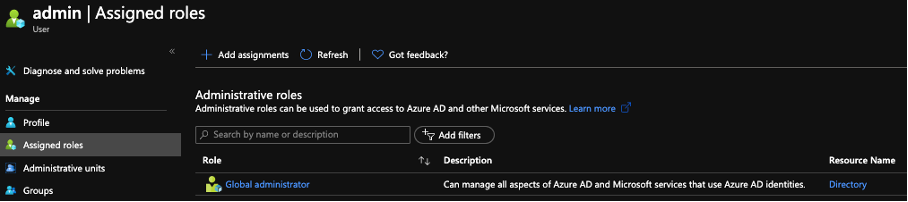
To use it, an account must be created in AAD, and Global Administrator rights assigned to it. From then on, authenticate the connector with that account.
In our example, we directly entered the information for a user. In fact, this information can be retrieved in different ways. The recurring flow is triggered as follows:
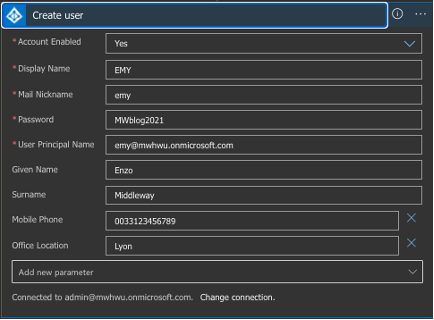
We entered the following information in the Azure AD shape:
The “User Principal Name” parameter must be unique. As indicated below, we now have a user created in the AAD, where the tenant is mwhwu.

The Azure AD connector cannot be used to access the AAD B2C. Microsoft Graph API (graph.microsoft.com) or Azure AD Graph API (https://graph.windows.net/{tenant_id}{resource}?{version}&query-parameters) must be used.
For testing purposes, we constructed the workflow as follows:
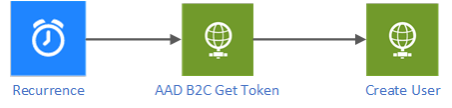
The following steps are required:
Add an app registration to Azure AD B2C and create a client_secret for this app registration. Note: the necessary permissions must be granted.
For more information on permissions, see here.
Then, we can access Microsoft Graph/Azure AD Graph through the Logic Apps via an HTTP action.
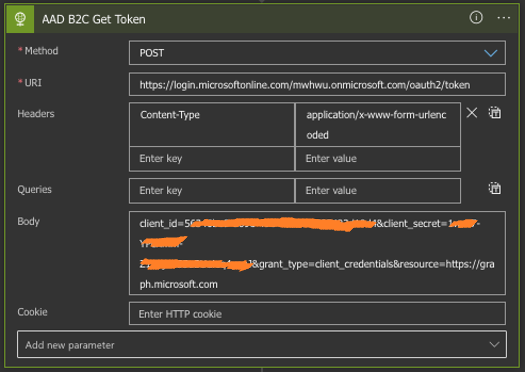
POST a message to the URI https://login.microsoftonline.com/tenant/oauth2/token, with the tenant: mwhwu.onmicrosoft.com, and with content-type application/x-www-form-urlencoded. In the body of the message, enter client_id and client_secret that we created in Step 1. At the end of this step, we will obtain an access_token that will be valid for one hour.
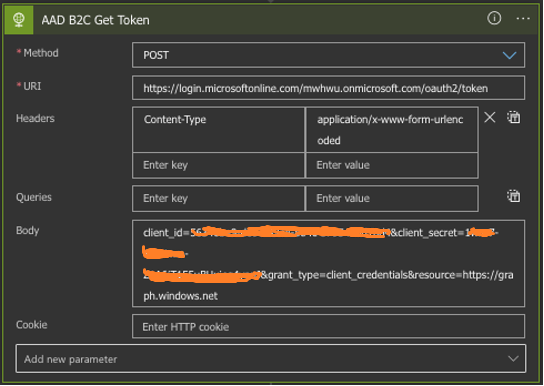
We can use the access_token obtained at Step 2 via Authorization Header to create an account in AAD B2C. As explained above, we use the user information directly in the Logic Apps. For information, all the properties we can assign when creating an account are listed here.
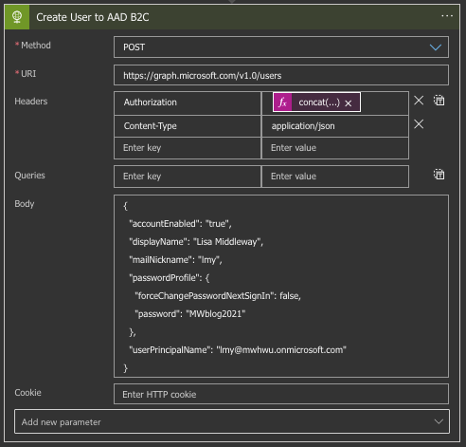
In AAD B2C, we have this account:
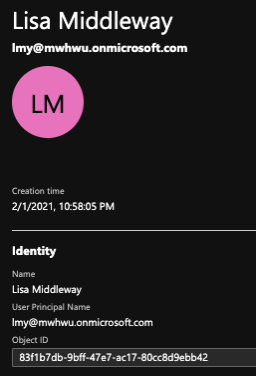
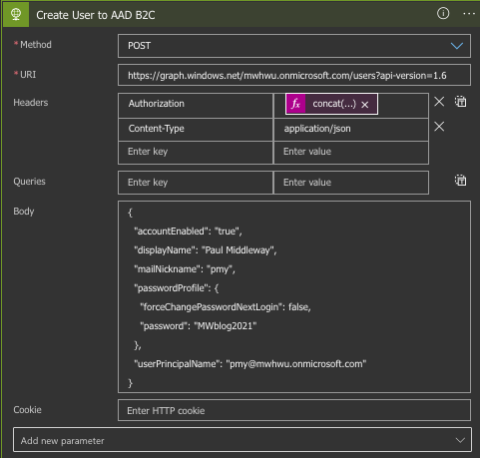
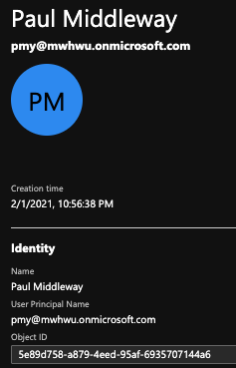
We have the account in AAD B2C:
We can describe the flow as follows:
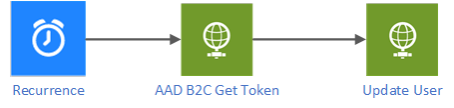
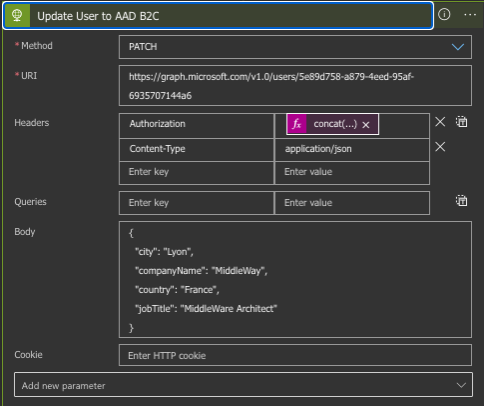
We are going to change a user’s city and occupation (the URI being https://graph.microsoft.com/v1.0/users/ObjectID) with the PATCH method.
Here is the result in AAD: